Acunetix WP Security (formerly known as WP Security Scan) scans your whole installation of WordPress for common security vulnerabilities. Install the plugin for your blog and visit its dashboard page. If the plugin detects vulnerabilities in your installation, then the dashboard page may show you any of the following mentioned security alerts:
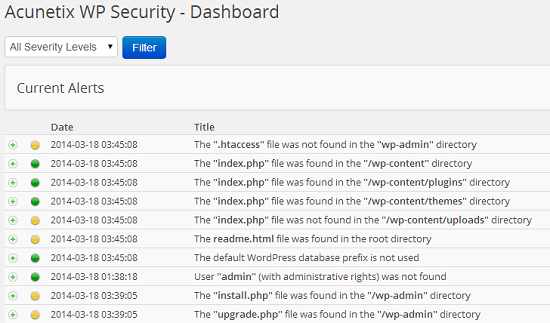
- Whether /wp-admin/ directory of your installation contains a hypertext access file: .htaccess (hypertext access) file is actually a configuration file which allows you to specify the configuration settings for a particular directory of your website or hosting account. Web servers generally have their own main configuration settings and a hypertext access file is used to override those settings.
- Whether /wp-content/, /wp-content/plugins/, /wp-content/themes/ and /wp-content/uploads/ folders of your installation contains a blank html file: An empty index.php or index.html file protects important directories of your installation from an attacker by disabling directory indexing (browser requesting a URL that points to a directory structure instead of an actual webpage within the directory).
- Is there a html file present in the root directory of your domain: Whenever you install WordPress manually or using an auto-installer, its root directory contains a readme.html file. This file do not contains any type of content which can be executed or can be exploited by an attacker. However this file contains the current version number of your CMS and it is suggested that you should either delete this file or make it completely inaccessible to all front end users. You can delete the file either manually or the plugin can do this for you provided that Empty the content of the readme.html file from the root directory is checked on the plugin’s settings page.
- Whether you are currently using the default database prefix (wp_): Many experts consider this as a security vulnerability, as it make your installation more prone to SQL injection attacks. Renaming the table prefix of your installation makes it harder for an attacker to guess the table name.
- Whether there is a user in your installation whose username is admin: If your installation contains a user whose username is set to admin (a commonly used username in many CMS) and who also have full administrative rights in your blog, then you are making your blog vulnerable to brute force as well as dictionary attacks, which are sophisticated attack techniques used to guess password.
- Whether your installation contains php and upgrade.php files: The /wp-admin/ directory of your installation contains install.php and upgrade.php files, which are used to install and upgrade WordPress, and direct access to these files must be restricted. Either you can permanently delete them or change their permission (CHMOD) to 000 (completely deny read, write and execute rights to everyone including yourself).
- Whether you are currently using the latest version of WordPress: Using the latest version of the CMS not only provides you with new features, but also provides you with latest security updates and patches. You can always check the version number of the latest installer of the CMS right here: http://wordpress.org/download/.
- Whether front end users can see the existing version of WordPress that you are currently running: If yes, then a hacker or an attacker may easily get into your installation by exploiting the vulnerabilities present in the current version of WordPress. If you visit the source code of any page of your site, you can see the version number of WordPress under <meta name=”generator” content=”WordPress X.X.X” />. The plugin can remove this meta tag for you provided that Remove various meta tags generators from the blog’s head tag for non-administrators option is checked on its settings page.
- Whether all your blog’s registered users can see theme, plugin, core and admin notifications in their dashboard: These notifications are generally displayed at the top of WordPress dashboard and they should be visible to blog administrators only. Check the box in front of Remove core update notifications from back-end for all but administrators, Remove plugin update notifications from backend and Remove themes update notifications from backend on plugin’s settings page to stop displaying update notifications.
- Whether RSD (Really Simple Discovery) tag is displayed to front end users: RSD tag allows WordPress bloggers to communicate with other third party services using XML-RPC (eXtensible Markup Language Remote Procedure Call) protocol. If you don’t have any requirement to use this protocol, then you should disable RSD meta tag from the front end. The plugin can automatically remove this tag for you provided that Remove Really Simple Discovery meta tags from front-end is checked on the plugin’s settings page. A typical RSD tag in WordPress looks like: <link rel=”EditURI” type=”application/rsd+xml” title=”RSD” href=”http://www.yourdomain.com/xmlrpc.php?rsd” />.
- Whether Windows live writer tag is displayed to all front end users: WLW tag allows blog authors to write content using Windows Live Writer and other third party blogging clients. If you don’t use blogging clients to write content in your blog, then the plugin can remove WLW tag for you provided that Remove Windows Live Writer meta tags from front-end is checked on the settings page. A typing WLW tag in WordPress looks like: <link rel=”wlwmanifest” type=”application/wlwmanifest+xml” href=”http://www.yourdomain.com/wp-includes/wlwmanifest.xml” />.
- Whether all users can see login errors: If Remove login error notifications from front end is checked on the settings page of the plugin, then the plugin will remove all types of login errors from your blog’s login page, whenever someone tries to login to your dashboard and their login attempt fails.
- Whether errors related to PHP and Database of your blog are visible to your blog’s registered users: These errors are only meant for administrators and in order to get rid of these errors, simply check the box in front of Disable error reporting (php + db) for all but administrators on plugin’s settings page.
- Remove the version parameter from URLs: Enabling this option from the settings page of the plugin allows you to remove the version number of various JavaScript and CSS files present in your blog. The version parameter in WordPress is generally added by wp_enqueue_script and wp_enqueue_style functions. However keep in mind that after enabling this option, your website may break and if that happens, then you should turn this option off.
Database Page
The Database page of the plugin allows you to backup your blog’s existing database as well as change the table prefix of your installation:
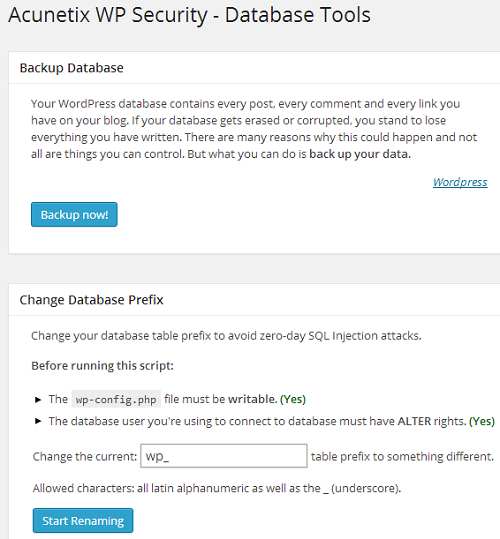
The database of your blog contains EVERYTHING like the content of your posts and pages, hyperlinks, plugin settings etc. There can many reasons because of which your database might get erased or corrupt, so backing up your database regularly is very essential.
And if you want to change the table prefix of your database, then always keep following things in mind:
- Create a full backup of your database beforehand and download the backup file onto your computer’s hard drive.
- Make sure that your installation’s wp-config.php file is writable (with CHMOD 755 or 775 or 777). If it’s not writable, then the script execution will fail. If you don’t know how to make a particular file writable, then contact your host and they will change the permission of the file for you.
- The user who is trying to run the script must have ALTER rights in the database. If ALTER rights are not present for a particular user, then he can’t execute the script. You may want to contact your web host, if you’d like to know whether a particular user have ALTER rights or not.
WP Info Page
Visiting the information page of the plugin allows you to see following details about your account/server:
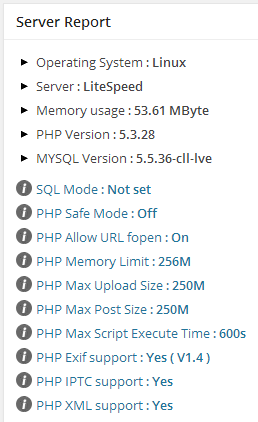
- Name of operating system that your server is currently running like Linux, Windows etc.
- Type of server like Apache, LightSpeed etc.
- Amount of memory currently being used by your installation.
- Version of PHP and MySQL that your server is currently running.
- Current status of SQL mode, PHP safe mode and PHP allow URL fopen.
- PHP memory limit: This field shows you the maximum amount of memory that a particular script is allowed to consume on your server. By using a realistic value for memory limit in this field, you can protect your server as well as all your installed applications from DDoS (Distributed Denial of Service) attacks and bugs like infinite loops etc.
- PHP Max upload size: This field shows you the maximum size of a file that can uploaded to your account. A realistic limit is quite useful in mitigating damages when an attacker tries to send huge files to your server, so that its resources can be exhausted.
- PHP Max post size: This field shows you the maximum size of any post request that PHP will process on your server. Any value above this limit will be rejected by your server.
- PHP Max script execution time: A script is allowed to run for a limited time (in seconds) on your server. After this your server will automatically terminate the script. A realistic value ensures that your blog’s scripts do not consume too much of CPU and RAM on your server.
- PHP Exif support: The information in this field shows you whether you can work with metadata (data about data) of images. Metadata of an image includes information like type of camera used, owner’s name, exposure value etc.
- PHP XML support: This field shows you whether PHP on your server is capable of handling extensible markup language (XML).
This page will also show you the current as well as the suggested file permissions (CHMOD) for your installation’s core files and folders. If you see an exclamation Mark in front of a file or folder name, then chances are very high that you are required to apply a more restrictive permission for that particular file/folder:
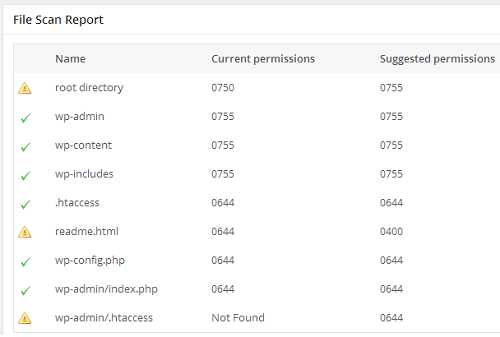
WP File Scan
The file scan page of the plugin first tries to identify the version of WordPress that you are currently running in your hosting account and after that it checks/compares all your installation’s core files against the officially released version of the CMS. This is done so that the plugin could determine how many and what files were modified during the selected time interval:
If the plugin detects any modifications, then it will notify you the filename in the scan results.
Important Notes:
- After running the script that can change the prefix of your blog’s database table, you are required to change the permission of wp-config.php file back to 0644 (The file’s owner can read and write; Users in the same group as the file’s owner can read and All users can read) or something more restrictive. Do not keep a file writable with 0777 permission (everyone can read, write and execute), as it’s a security risk.
- The renaming process is absolutely flawless, but if you start seeing database errors on your site, then you should restore your database using the backup file you downloaded earlier. For restoring the file either you can use phpMyAdmin or provide the backup file to your host.